An Internet facing Exchange server is said to be an Open Relay if, it accepts emails from any sender and delivers it to any recipient no matter if the recipient exists or not.
For eg: Consider that you have an Exchange Organization setup for the domain xyz.com. A user jim@abc.com sends an email to roddick@efg.com through your Exchange Server. The server accepts the email even-though the domain and user mailbox is unknown for it. Such a set up can be extremely vulnerable to attacks and is not considered as a best practice.
Thus, from the above example you will get an idea that an Exchange Organization which is built upon the Best Practices will be configured only to accept emails from external senders to recipients that are either members of the Exchange Organization or an Accepted Domain [known domain].
Tests to find if an Exchange Server is an Open Relay :-
- TELNET TEST: This is a simple test can be performed from the command line. We will try to send an email to an unknown user and check if the server accepts it or not.
- Start Command Prompt (CMD) by searching in Windows
- Type telnet and press Enter
- Once in telnet prompt, type set localecho
- Then type open [external ip/name] 25 eg: open 20.30.40.50 25
- Following response will be received ‘220 mail.server.domain Microsoft ESMTP MAIL Service, Version: 6.0.2790.0 Ready at’
- Type the command : ehlo firsttestdomain.com [Make sure that ‘firsttestdomain.com‘ is anything other than the domain your Exchange Server handles]
- Select OK and you will receive the following :250 OK
- Type the command mail from:user@firsttestdomain.com [Note, this email address is not a mailbox in the Exchange Server]
- Select OK and you will get the response
250 2.1.0 user@firsttestdomain.com….Sender OK - Type the command rcpt to:user@secondtestdomain.com [completely a new address not mentioned above]
- Once you select OK, you will receive a response and depending on that response we can determine if the server is an open relay or not:
If the response is
550 5.7.1 Unable to relay for user@secondtestdomain.com means, your server is not an open relay & is secure
At the same time, if the response is
250 2.1.5 user@secondtestdomain.com means your server is un-secure and is an open relay.
- DNSBL DIAGNOSTIC TEST : An alternative and a quick solution to determine open relay is by checking the domain against any of the DNS Block List providers such as MXTOOLBOX.COM.
- Access the website MXTOOLBOX.COM
- Select the SMTP DIAGNOSTICS tab
- Enter your mail server IP address or external name and select the Test Email Server tab
- You will receive a response stating whether the server is an open relay or not as shown in below eg:
CAUSES OF OPEN RELAY :-
The main causes that can turn an Exchange Server to an Open Relay is the configuration issues with the connectors and Accepted Domains. The following checks can be done on this regard:-
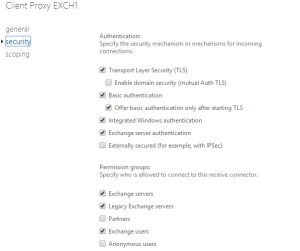
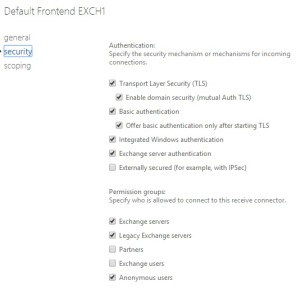
- If ‘Externally Secured‘ option is enabled on the Internet Send/Receive connectors.
In the Exchange Management Console, Send Connectors can be found in Hub Transport role under Organization Configuration while, Receive Connectors in Hub Transport role under the Server Configuration. Make sure that in the properties -> Authentication section of these Internet connectors, the Externally Secured option is disabled in order to stop your Exchange Server being an Open Relay .
- If Accepted Domains configured as ‘*’
In the Exchange Management console, Accepted Domain comes in Hub Transport role under Organization configuration. Accepted Domains are the domains that are known to the Exchange Server. The domains can be either Authoritative or Non-Authoritative. Make sure that no Accepted Domain are configured as ‘*’ to help protect your Exchange Server from being an Open Relay.
CLOSING AN OPEN RELAY ON EXCHANGE SERVER 2007/2010:-
The following command can be executed on Exchange Management Shell to disable Open Relay on an Exchange Server.
Get-ReceiveConnector “YourReceiveConnectorName” | Remove-ADPermission -User “NT AUTHORITY\ANONYMOUS LOGON” -ExtendedRights “ms-Exch-SMTP-Accept-Any-Recipient”
as per the link http://alanhardisty.wordpress.com/2010/07/12/how-to-close-an-open-relay-in-exchange-2007-2010.