VPN or Virtual Private Network can be established using a Windows Server in the network. Two main application scenarios of VPN are:
- Remote Access VPN [ Clients connecting to corporate network ] – Makes use of PPTP, L2TP, SSTP tunnel etc.
- Site-to-Site VPN [ Branch office connecting to Head office ] – Makes use of PPTP, L2TP, IPSec Tunnel mode etc.
One of our client has a VPN server and the tunnel type which is configured is SSTP [ Secure Socket tunneling Protocol ]. This tunnel type makes use of SSL 3.0 channel to send PPP or L2TP traffic. It uses a SSL certificate for security and data encryption.
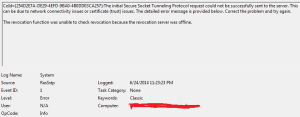
A remote user was unable to connect to VPN due to the error “The revocation function was unable to check revocation because the revocation server was offline”
You will also note below event logs in the client machine
Perform the following checks on the server
- On the Routing and Remote Access settings, check and confirm the type of tunnel being used is SSTP and that a public certificate is assigned
- Confirm that the SSL certificate is bound to the Default Web Site in IIS for HTTPS [port 443]
- Confirm certificate binding for IPV4 and IPV6 ( ie, 0.0.0.0:443 & [::]:443 ) using the command ”netsh http show ssl”
- Confirm the presence of SHA1 and SHA256 certificate hash in registry at the locations ”HKLM\ System\ CurrentControlSet\ Services\ Sstpsvc\ Parameters\ Sha1CertificateHash” and ”HKLM\ System\ CurrentControlSet\ Services\ Sstpsvc\ Parameters\ Sha256CertificateHash” respectively
Note: In case if you notice that the certificate hash or netsh bindings is not the same or if IPV6 binding is missing you will have to reset the bindings.
- To delete the certificate binding for IPV4, use command ”netsh http delete sslcert ipport=0.0.0.0:443”
- To delete the certificate binding for IPV6, use command ”netsh http delete sslcert ipport=[::]:443”
- Delete certificate binding in RRAS config, by deleting the registry keys ”HKLM\ System\ CurrentControlSet\ Services\ Sstpsvc\ Parameters\ Sha1CertificateHash” and ”HKLM\ System\ CurrentControlSet\ Services\ Sstpsvc\ Parameters\ Sha256CertificateHash”
- Use the command ”netsh http add sslcert ipport=0.0.0.0:443 certhash=xxx appid={ba195980-cd49-458b-9e23-c84ee0adcd75} certstorename=MY and netsh http add sslcert ipport=[::]:443 certhash=xxx appid={ba195980-cd49-458b-9e23-c84ee0adcd75} certstorename=MY”, where xxx is the certificate hash of the trusted certificate
- Check and confirm that no error is received when accessing the CDP (CRL Distribution Points) url “https://remote.your_domain.com/sra_{BA195980-CD49-458b-9E23-C84EE0ADCD75}/“
At this point we have done with the checks from the server end. Now, check the settings in the client machine.
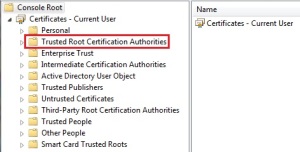
- Confirm that the SSL certificate is installed in the Trusted Root Certification Authorities of the client machine
Note: For SSTP VPN connections, by default, the client must be able to confirm that the certificate has not been revoked by checking the server identified in the certificate as hosting the certificate revocation list (CRL). If the server hosting the CRL cannot be contacted, then the validation fails, and the VPN connection is dropped. To prevent this, you must either publish the CRL on a server that is accessible on the Internet or configure the client to not require CRL checking. To disable CRL checking, create a registry setting at the following location:HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Sstpsvc\parameters. The setting must be a DWORD value named NoCertRevocationCheck. Set the value to 1.
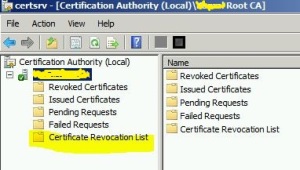
As mentioned in the above technet article, either we should place the CRLs in the Certificate Revocation List in the local machine or disable the CRL checking by making the above registry modifications.
If you are not interested in registry modifications, you will have to export the CRLs from Certificate Authority on your server and import it to the CRL location in the client machine.
To launch the Certificate Authority console execute certsvc.msc /e in Run program.
- You might also have to make necessary changes in Internet Explorer to disable automatic proxy settings
- Test and confirm VPN access
Note: – The same VPN issue can also occur sue to expired CRLs
Reference :
- http://social.technet.microsoft.com/wiki/contents/articles/15552.troubleshooting-fim-cm-error-0x80092013-revocation-function-was-unable-to-check-revocation.aspx
- http://www.c7solutions.com/2009/03/configuring-sstp-vpn-on-small-business_31-aspx