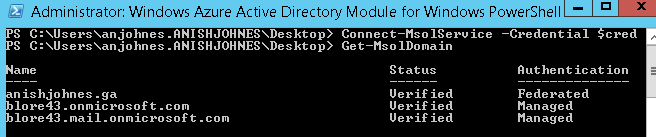
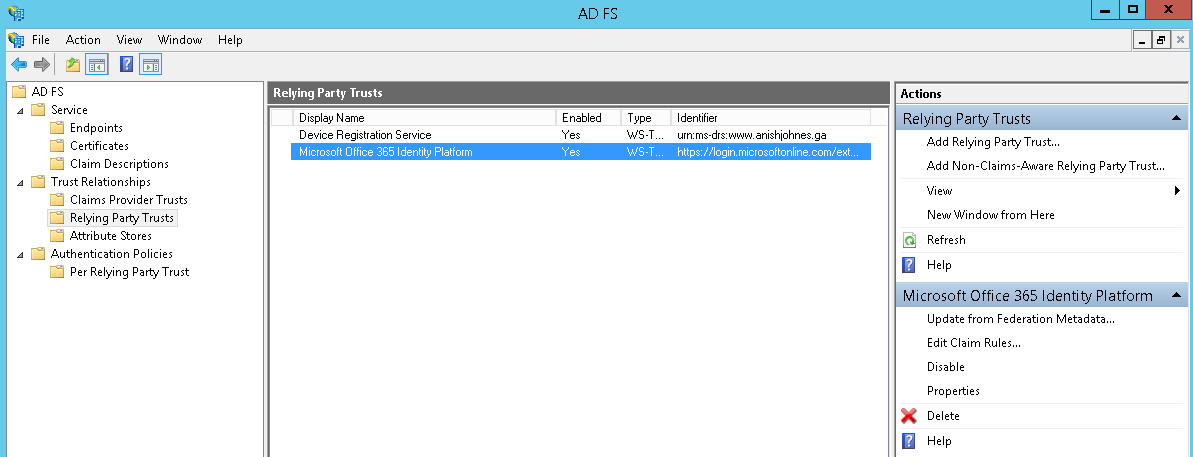
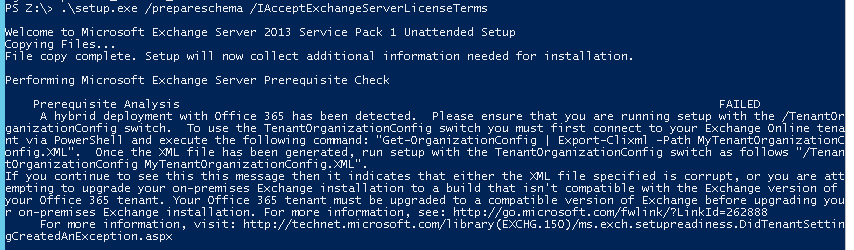
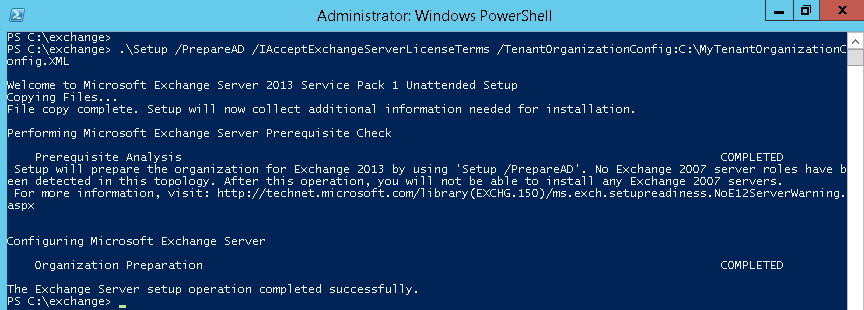
As part of an Exchange Server recovery, the Edge Servers were re-subscribed to the AD site and HCW was ran. The HCW did complete, but threw some warnings towards the end as shown below:
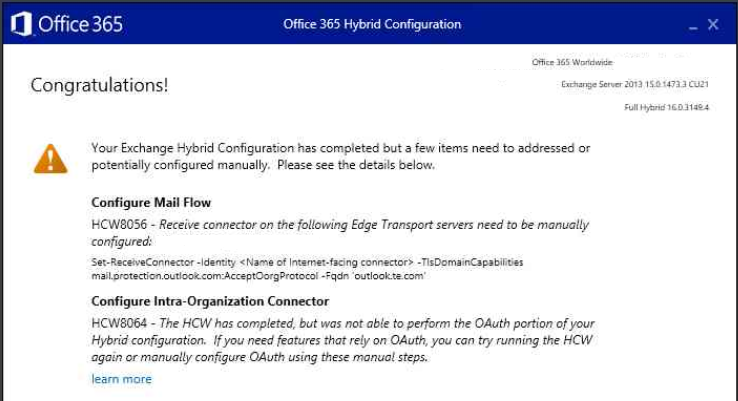
The warning HCW8056 was ignored as the receive connectors on both the Edge Transport servers were already setup correctly. At the same time, I was little bit sceptical about the warning HCW8064 and thought of going ahead with the post-checks. The link “learn more” pointed to this MS article.
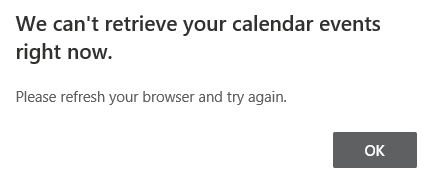
After the mail flow checks were successful, next part was to perform free-busy checks. This is when I noticed that the free-busy from O365 to Exchange on-premises was failing with below error. The free-busy from Exchange on-premises to O365 worked fine however.
For free-busy to work correctly there are couple of checks performed by the Availability Service on Exchange Online in the following order :
a) Intra-Organization Connector [OAUTH] (for Exchange Server 2013 CU5+)
b) Organization Relationship [DAUTH]
c) Availability Address Space
To understand more about how hybrid free-busy works please read this Microsoft Exchange Team Blog.
Upon checking the Intra-Org connector status on cloud we noticed that it was showing as disabled.
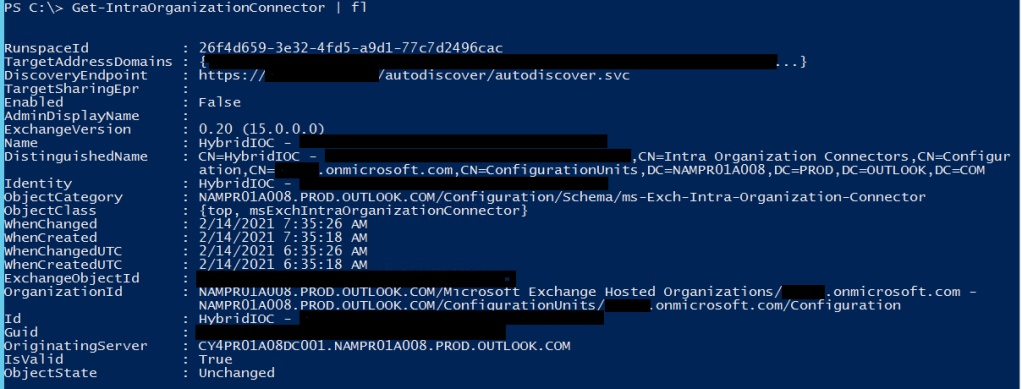
This confirmed why the free-busy was failing and can be fixed by executing the below command on cloud:
Get-IntraOrganizationConnector | Set-IntraOrganizationConnector -Enabled $true
Make sure the Intra-Org connectors are enabled at the On-Prem side as well for On-Prem to cloud free-busy to work correctly.
Note: As a workaround, instead of enabling the Intra-Org connector on cloud you can update the TargetSharingEpr value on the Organization Relationship in cloud with the On-Premises Exchange servers EWS ExternalUrl endpoint.